Discover the ins and outs of Tokenization and how it impacts businesses
Have you heard of tokenization and how it applies to businesses? No worries if you haven’t. We’re here to break it down for you. If you run a business, this article is a must-read. No business is safe from the risk of security breaches. Not even small businesses. Tokenization helps mitigate that risk.
Seamless integration, effortless payments
Keep business running smoothly. Our solutions integrate with popular programs
In this article we’ll cover:
- What tokenization is
- How it works
- What encryption and de-tokenization are
- How tokenization benefits businesses
- And more!
Every business has its own set of challenges. Some struggle with employee retention while others lose customers to their competition. There are problems that are industry-specific and then there are supply-chain issues. Managing a business is not easy. That’s why there are tools and procedures to simplify operations and resolve matters.
At Acumen Connections, payment gateway Wichita, we believe that the success of a business depends on a wide range of factors. From quality control to customer satisfaction, there are multiple areas that a company needs to monitor, including security. This is where tokenization comes into play.
What is tokenization?
Tokenization in simple terms is the process of exchanging sensitive information for non-sensitive information, or “tokens,”.
The tokens here are basically decoys that contain some pieces of the original data such as similar length or format. They are used in place of the real data to continue business operations while the original data is securely kept off the organization’s systems. Tokenized data can’t be read or used anywhere.
It’s a growing field becoming more popular by the day. By 2026, the global tokenization market is expected to be worth $5.6 billion.

Tokenization and business security
As a business owner, you’re likely to think along the lines of investment versus returns. In fact, you’re probably wondering if this new security measure is going to cost an arm and a leg. More importantly, you want to know if it is worth the money.
We asked Software Development Manager, Erick Coble, if tokenization is worth investing in from a business standpoint. He responded, “Most definitely. Tokenization greatly reduces the risk of data loss in the event of a breach. Data loss can become costly and substantially harm a company’s credibility.”
When it comes to business as a whole, one of the most common forms of tokenization can be found within e-commerce payment processing. Here, tokens are used to replace account or card numbers. Three of the biggest vendors in the US tokenization sphere are Visa, Mastercard, and American Express.
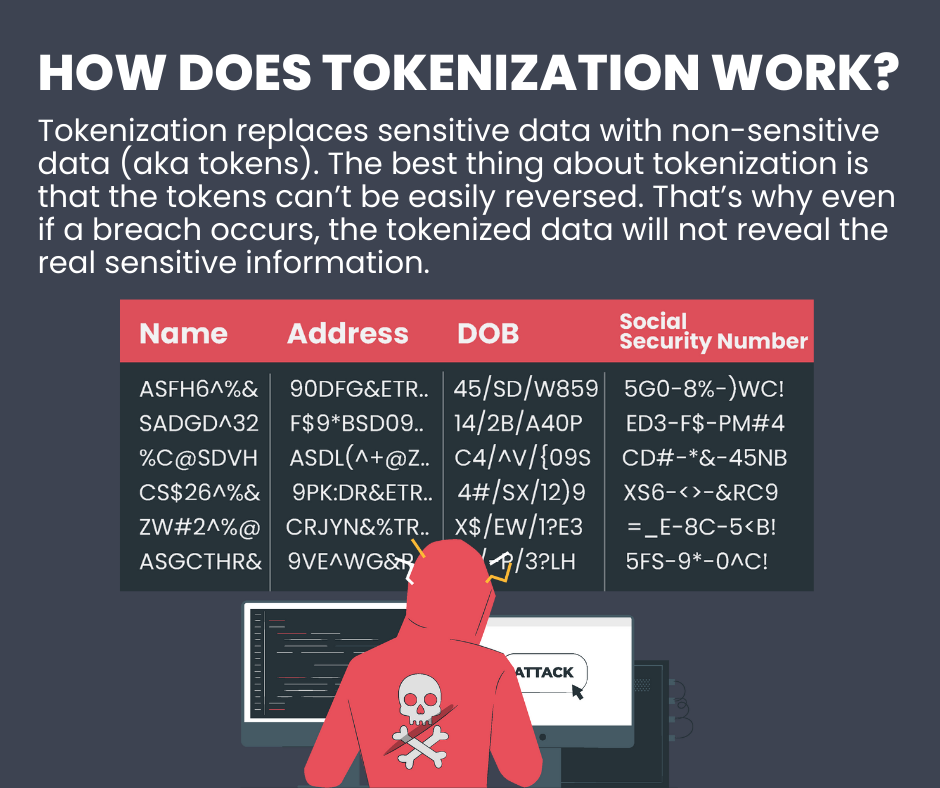
How does tokenization work?
Tokenization replaces sensitive data with non-sensitive data (aka tokens). Most organizations have sensitive data stored in their system. For example, a bank has customers’ debit card information or social security numbers. By using tokenization, they can run their day-to-day operations uninterrupted minus the risk of data theft ramifications.
The best thing about tokenization is that the tokens can’t be reversed. They can’t be easily reverted to the original sensitive data. That’s why even if a breach occurs, the tokenized data will not reveal the real sensitive information.
Erick adds, “It is a safe bet that eventually your company will be targeted by hackers. It is critical that you have the proper measures in place to stop loss of data as well as make yourself an unsavory target by not supplying the information the attackers want.”
Understanding what encryption is and how it works
Mathematically changing sensitive data while retaining its original pattern within the new code is called encryption. This data can be decrypted by using an appropriate key.
In simple terms, encryption works by employing mathematical algorithms and digital keys. A “cipher” or encryption algorithm along with an encryption key is used to encode sensitive data. This encoded data is transmitted to the recipient who can only decipher this data by using the designated key. Only the right key can decipher the encrypted data.
Here’s a tokenization example:

How tokenization works in banking
Tokenization has great significance in the banking and financial services industry. The databases of banks are likely to hold information such as bank account numbers, credit or debit card details, transaction history, etc. It can cause major problems if data of this nature falls into the wrong hands. Hence, tokenization is used to remove the account numbers and replace them with dummy characters or tokens.
“Attacks and data breaches have become more prevalent and will continue to grow as long as hackers are able to achieve their goals,” Erick explains. This is evident for finance and banking industries. They’re often the target of a lot of these schemes.
However, in truth – any business that houses customer data poses a risk.
Detokenization explained
Simply put, detokenization is the reverse of tokenization. It involves exchanging tokens for original sensitive data. We have explained that tokens can’t be reversed. Detokenization can be achieved through the original tokenization system only.
Vault vs Vaultless
One thing of importance to note is that when it comes to detokenization, there are actually two types of tokens: vault and vaultless. One of them cannot be detokenized.
Vault tokens have no value. They cannot be detokenized. They’re only used internally to reference sensitive data. That sensitive data never leaves the network.
On the other hand, vaultless tokens use cryptographic devices to create conversions. These are used to transfer sensitive data into and out of the token. Vaultless tokens allow the sensitive data to leave the network in a secure way.
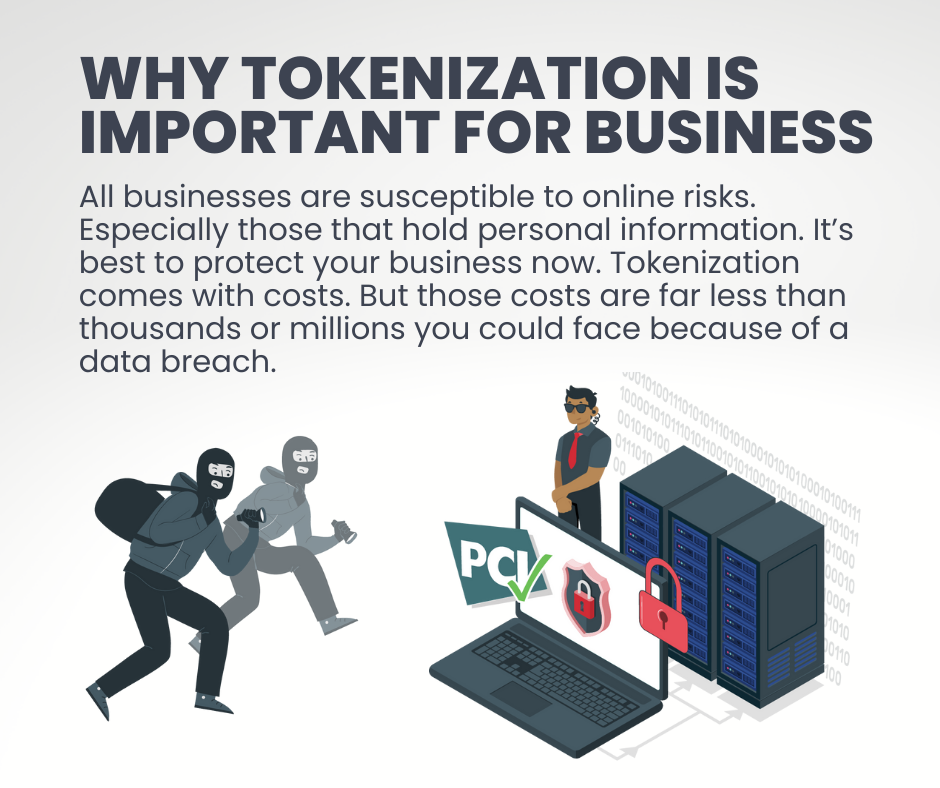
Why is tokenization important for companies?
Tokenization is important for companies because it prevents unwanted events like identity, data, or financial theft from happening.
All companies are susceptible to human error, employee fraud, phishing, data breaches, and cyber-attacks. That’s why cybersecurity for businesses is an essential requirement to avoid all kinds of fraud.
Tokenization ensures that there is no sensitive information available to steal even if a data breach happens. Tokens can’t be used by hackers since they can’t be reversed to the original data.
“It is a safe bet that eventually your company will be targeted by hackers, and it is critical that you have the proper measures in place to stop loss of data as well as make yourself an unsavory target by not supplying the information the attackers want,” Erick recommends.
Did you know the average cost of a data breach is $4.24 million?
What type of businesses would benefit from tokenization?
Erick answers, “Any business that retains PII (Personally Identifiable Information) should be substituting sensitive information with tokens where applicable so that sensitive information is never exposed to external sources.”
We asked if there are any potential downsides to tokenization and Erick pointed out that although the cost of investment can be a deterrent for some, the long-term cost of not investing in tokenization can be higher.
Is tokenization feasible for small businesses?
Oftentimes what’s applicable to large corporations may not work for small businesses but that’s not always the case. We asked Erick to shed some light on the subject and he said, “Tokenization is a sound investment for any company to make because it benefits the company by establishing trust with the consumer, strengthens security, and significantly reduces the risk of future costs associated with loss of data.”
Other examples of tokenization
You might be thinking “I’ve heard tokenization used in other ways – like NFTs”. How else can tokenization be applied?
“Blockchains” play a big role in cryptocurrency systems. The types of tokenization we’ve talked about so far have been “outside of the blockchain”. They’ve been outside of the realm of cryptocurrency.
However, tokenization can be used in many ways – including in crypto. Let’s examine tokenization in blockchain.
How tokenization works in blockchain
In blockchain, tokens are used as digital representations of assets.
It’s the process of converting an item into a valuable digital token. For instance, the ownership of a company is made up of shareholders. Each share can be represented by a token.
This has tremendous potential in real estate since the buying and selling of properties can be a hassle. Tokenization will simplify the process and allow for speedy transfers of ownership.
The same can be said for cryptocurrency and NFTs.
How tokenization works in crypto
Tokenization in crypto is done to facilitate fast and transparent transactions. It optimizes the process of trading ownership. There is no having to wait for a middleman, certain open hours, or other factors that impact the speed to transfer.
Crypto tokens allow value and information to be stored, transferred, and verified in a secure manner. They are used to signify ownership of shares in a company or access to a product or service. At times, crypto tokens are used as currency.
How tokenization works in Python
n Python, tokenization splits up a text document into smaller units or terms. Each of these is a token. It is often used in natural language processing (NLP). Learn more with Analytics Vidhya.
The last word:
To quote a saying as old as time: prevention is better than cure.
It is relevant to just about any situation in life. It is almost always easier to avoid something undesirable than to get rid of the same. Tokenization is an essential preventative measure that businesses need to consider. It would help fortify their systems against data breaches and the plethora of problems that would follow.
We highly recommend consulting the following pages:
Anna Reeve, MBA










